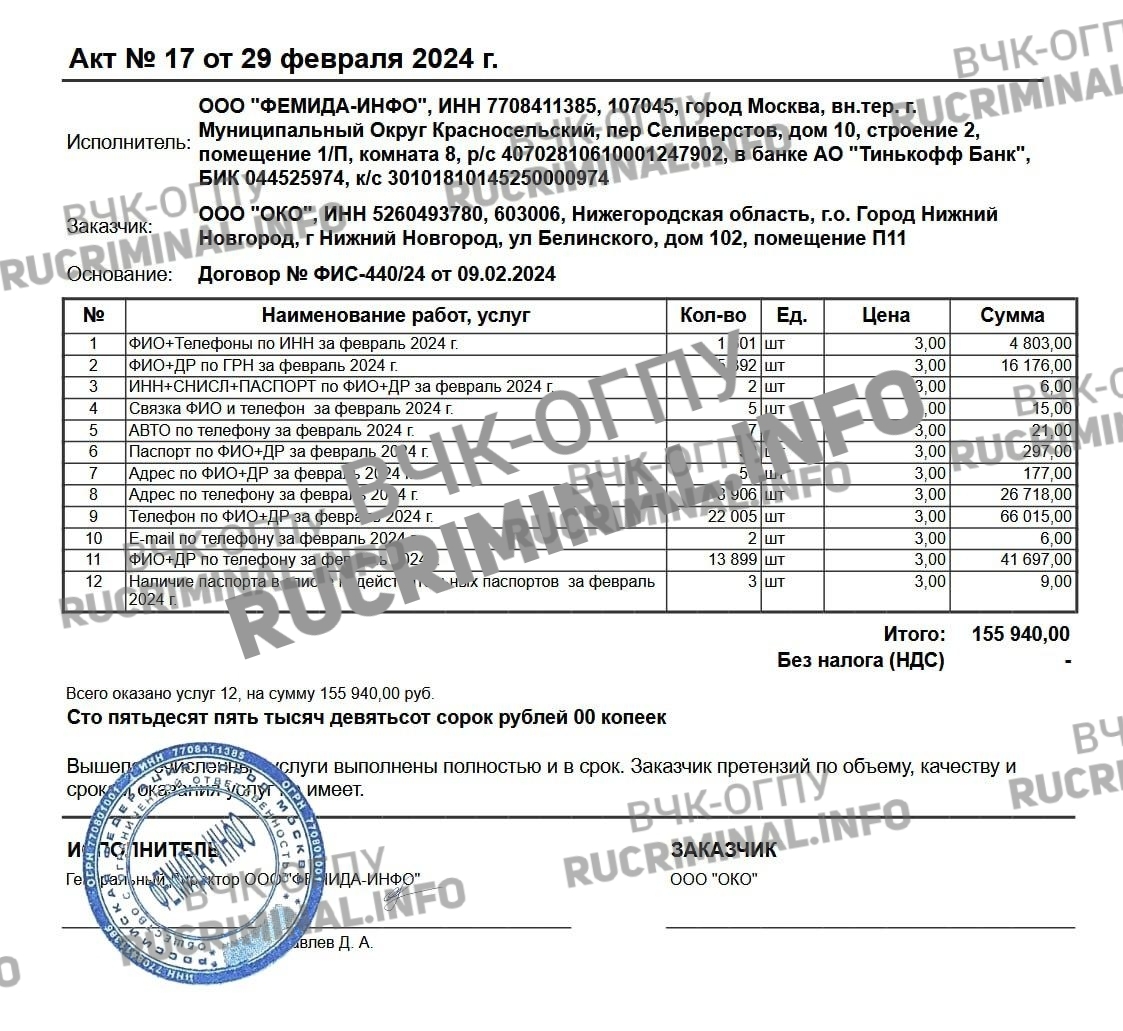
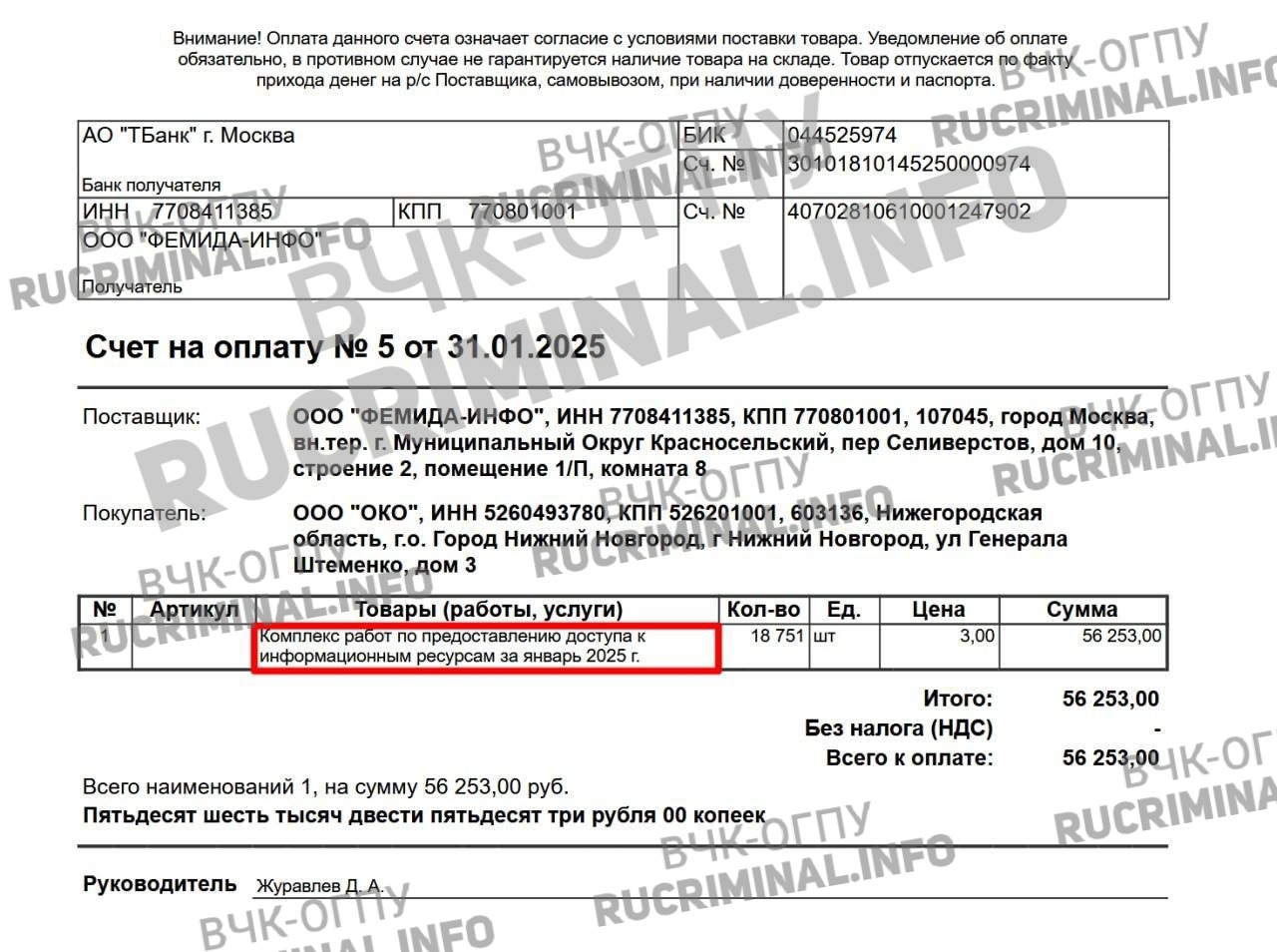
Multiple sources at the VChK-OGPU and Rucriminal.info reported that the userBox data-mining bot and its creator, Igor Morozkin, were simply used by a single group of "monsters" who mine personal data for people who exist without any problems on Telegram and the internet. This group, consisting of Himera Search, Odyssey Search, and Femida, operates as a single entity and controls the bulk of the data-mining and illegal access market for citizens' confidential information, and is also closely connected to Russian security forces. Through userBox and Morozkin, who wanted to be "like Pavel Durov" (as he says in the audio we are publishing), they launched the most problematic databases, and the group then claimed to have purchased these databases on the "market"—that is, from Morozkin and userBox. This was the case, for example, with the KORDON database. "KORDON" is a photo-recording system for citizens in passport control booths at border crossings, with access to up-to-date data until 2025.
Sources indicate that the "KORDON" database was legitimized through a controlled "leak." Initially, data on "defected" and opposition-minded citizens was published, and the full database first appeared in Morozkin's UserBox. Only after that did Himera claim to have "bought" it "on the market." Our sources claim that the initial source was an official access point within the BSTM/FSB structure, and UserBox was used as a cover and a point of legitimization.
Ultimately, Morozkin was simply "leaked" as a person no longer needed, and now all the high-profile recent leaks are being pinned on him.
The editorial office has learned details about the operation of the closed system for checking and accessing official government databases.
The origins can be traced through Odyssey Search, where, after the director's replacement, Lolita Kristal, was replaced by Stanislav Mikhailovich Kirillov, connections with Sergei Kirillovich Ponomarev emerged. Both are involved in Himera Search, which was initially launched publicly, then went private and became the core of the network. The services are linked by the domains femida-search.ru, odyssey-search.ru, and himera-search.net/.biz, registered at the same addresses, shared developers, and formally listed top managers. The founders also have access to law enforcement officials.
A product known as Himera Black is particularly significant. This isn't about routine checks, but rather access to operational-level data: age and income filters, SIM billing, tower location, IMEI/IMSI, call details, border crossing history, and use of the KORDON database.
Sources also point to Solaris Inform, a closed access node that handles billing, car-sharing, COVID-19 databases, data from the Federal Tax Service, Rosreestr, the Russian Union of Motor Insurers (RSA), and the Sirena aviation system. The cost is approximately 2 rubles per request for a corporate subscription of approximately 150,000 rubles per month. Individual users can use Himera/Odyssey/Femida services with significantly higher rates.
Aside from Kirillov and Ponomarev, the other individuals involved in the scheme include Dmitry Alekseevich Zhuravlev (formerly a MUR employee, later a security officer for Yandex.Drive and Delimobil), Khakan Gadzhiakhmed Ogly Abulov (developed by Femida), and individuals connected through Grifoniks Invest—Alexander Yuryevich Medvedev and Ilya Sergeevich Ionov. Lolita Kristal (Kirillova), who is closely involved in the legal aspects of the scheme, is also visible in certain registers. At every stage, there's a connection to the Delimobil car-sharing service, where Kirillov was involved in the industry's largest leak, after which he disappeared from the public eye, and Himera soon emerged.

Himera has now become the dominant system in data breaches.
It's telling that Kirillov's Telegram account used the nickname Stas_272, which matches the criminal code for unauthorized access to computer information, which could be interpreted as deliberate irony.
Thus, the entire structure indicates that the Russian data breach market—including operator data, billing, movements, the Federal Tax Service, Rosreestr, Kordon databases, SIM and IMSI numbers—has not been destroyed or shut down by the state. It is centralized, monopolized, and operates under the cover of a structure that gained access through an administrative decision and the purge of competitors. Commercial monetization of proprietary data has become a fact, and access prices have skyrocketed following the elimination of independent players. Claims to combat leaks cover up the redistribution of control and income.